Microsoft no longer lets you decide whether to install Windows system updates, and online criminals have noticed. The new Fantom ransomware takes advantage of this situation by nearly perfectly mimicking the Windows Update process, and will keep almost any user fooled until it's too late.
What Windows Patches Needed to Prevent WannaCry Ransomware - What Windows Patches Needed to Prevent WannaCry Ransomware. What Windows Patches Needed to Prevent WannaCry Ransomware. Mac OS are not affected by this widely spread ransomware. Windows 10 Creators Update computers are also not affected by WannaCry since the operating system. To fix Windows SMB vulnerability that WannaCry ransomware is leveraging, Microsoft has just released an emergency security patch update for all unsupported versions of Windows (XP, Vista, 8, Server 2003 and 2008). So, if your organization, for some reason, is still running on Windows XP or Vista, you are strongly advised to download.
AVG security researcher Jakob Kroustek discovered Fantom last week. He notified the Bleeping Computer blog, and the details are pretty scary.
The ransomware itself is called 'CriticalUpdate01.exe,' the file it extracts is called 'WindowsUpdate.exe,' and the screen that displays as it begins to encrypt your files looks very much like the modern blue screen that Windows 8, 8.1 and 10 users are familiar with.
Free Ransomware Protection For Windows 10
'Unfortunately, there is no way to currently decrypt the Fantom Ransomware,' Bleeping Computer noted, adding that the ransomware was built using the open-source ransomware kit called EDA2.
Wannacry Windows Patch Download
MORE: What Is Ransomware and How Can I Protect Myself?
While you're waiting for Windows Update to finish and the machine to restart, Fantom is happily at work encrypting all the files it can find bearing any of about 600 different suffixes, including those commonly used for music, video, photo and office files. Encrypted files get the additional suffix '.fantom.'
When the encryption process is finished, Fantom pops up a ransom note instructing the user to email a Russian email address. No specific ransom amount is mentioned, but presumably the response from the online criminals will include one. Victims have a week to pay up or the files will be erased, the note says in pretty poor English.
If you're seeing that screen, you're pretty well hosed. Your only options will be to either negotiate a ransom payment (many of these crooks won't be offended if you try to haggle) or hope that any recent system backup you may have wasn't encrypted too.
To prevent infection by any kind of ransomware, don't click on any links in email messages you don't expect; configure your Windows user accounts so that your day-to-day-usage account is a 'limited' one that can't install software; and install and run robust, continually updating antivirus software.
Windows 7 and 8.1 users can go into Control Panel and set Windows Update to install patches only when they want it to. That won't prevent infection, but if a random Windows Update screen pops up, you'll know it's bogus and can shut down the machine immediately. (After that, boot antivirus software from a rescue disk — here area few you can burn to a CD or put on an USB flash drive — to clean your system without starting Windows.)

Windows 10 Home users can't stop automatic system updates. Microsoft, in its infinite wisdom, has taken away that choice from you. Even Windows 10 Pro users can only postpone, not opt out of, system updates. So if that Windows Update window takes over your screen, you won't be able to tell if it's the real thing, or ransomware.
Microsoft just released a patch for Windows XP that fixes a file sharing flaw being exploited by the WannaCry ransomware. Here's how to install it.
You can download some versions of the patch using links at the bottom of this May 12th Microsoft article: Customer Guidance for WannaCrypt attacks. The full list of patch variants, including languages other than English, is in the Windows Catalog, just search for KB4012598.
Windows Patch Download
For an x86 machine with Service Pack 3 installed, the downloaded file name is
windowsxp-kb4012598-x86-custom-enu_eceb7d5023bbb23c0dc633e46b9c2f14fa6ee9dd.exe
I know, its looks like malware itself. The file is small, only 665K. Logon as an Administrator and, for good luck, make a Restore Point first thing.
To see if System Restore is enabled, right click on My Computer, get the Properties and go to the System Restore tab. To actually make the Restore Point, go to Start -> Programs -> Accessories -> System Tools -> System Restore.
Windows Patch Download For Ransomware
The installation process is simple.
1. Wizard warns you to backup your system and close all open programs
2. Then you have to agree to a license
3. Installing the patch takes only a few seconds, even on old hardware. It first asks you to wait while it 'inspects your current configuration, archives your current files and updates your files.' Then it makes a restore point.
4. When its all done, it wants you to reboot
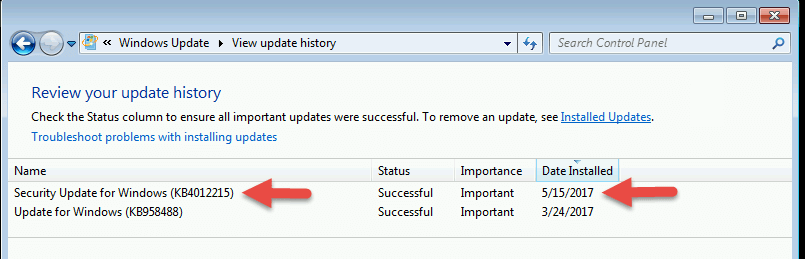
After rebooting, you can verify that the patch was correctly installed using Add or Remove Programs in the Control Panel. You first need to turn on the checkbox to 'Show updates.' Then scroll down looking for the 'Windows XP - Software updates' section. It should be huge.
In this section, look for 'Security Update for Windows XP (KB4012598)' with the current date as the date installed (see above). Considering this is Windows XP, the installation date should stick out like a sore thumb. On two machines that I tested, it was, fortunately, the last entry in the list.
The fix applies to the file sharing component of Windows (Server Message Block or SMB) and thus prevents an XP machine from being infected over a LAN (Local Area Network). However, it would not protect an XP machine that was attacked another way, via email, for example.
I checked around (here and here) and Microsoft has not issued an update to their free anti-malware software, Security Essentials, for Windows XP. When XP went off support, it was denied access to Security Essentials. Thus, XP machines remain vulnerable to WannaCry, just not via file sharing on a LAN.
To fully protect an XP machine requires a third party antivirus product. Lotsa luck with that.
BitDefender bragged today that they can protect against WannaCry, but they do not support Windows XP (see below for update). Neither does Avira, Trend Micro or F-Secure. Kaspersky still supports XP, but their website says nothing about WannaCry.

Windows Ransomware Protection
So, yes, Microsoft released a patch for Windows XP. But now you know the rest of the story.
UPDATE: May 15, 2017. A reader was nice enough to point out that Bitdefender does offer a product that supports Windows XP (and Vista too). The name is fairly direct: Security for XP and Vista.
Windows Ransomware Patch
UPDATE: May 15, 2017. A couple people have told me that when they verified the installation of the patch, the install date was not the current date but tomorrows date. Beats me why.
Ms17-010 Windows Patch Download
FEEDBACK
Ransomware Patch For Windows 10
Get in touch with me privately by email at my full name at Gmail. Public comments can be directed to me on twitter at @defensivecomput